Proxies 101: Everything Beginners Need to Know
Navigating the internet today often feels less like exploring a vast open space and more like walking through a series of gates and checkpoints. Every website you visit, every service you use, is constantly gathering information about you – and one of the most fundamental pieces of data they see is your IP address.
Think of your IP address like your home address online. It tells websites approximately where you are located and helps them send data back to your device. But it also means your online activity can be easily tracked, linked, and even restricted based on your location or past behavior.
For basic browsing, this might not be a big deal. But what if you need more control over your online identity? What if you want to access content not available in your region, enhance your privacy, or manage multiple online accounts without them being linked together?
This is where proxies come in. If you're just starting to explore how to gain more control and privacy online, understanding proxies is a crucial first step.
In this guide, we'll break down everything a beginner needs to know about proxy servers.
What Exactly is a Proxy Server? (The "Middleman")
At its core, a proxy server acts as an intermediary between your device (computer, phone, etc.) and the internet. When you use a proxy, your request to visit a website doesn't go directly from your device to the website. Instead, it goes like this:
- You send your request (e.g., "load google.com") to the proxy server.
- The proxy server receives your request.
- The proxy server then sends that request from its own IP address to google.com.
- Google.com sees the request coming from the proxy server's IP address, not yours.
- Google.com sends the requested data back to the proxy server.
- The proxy server sends the data back to your device.
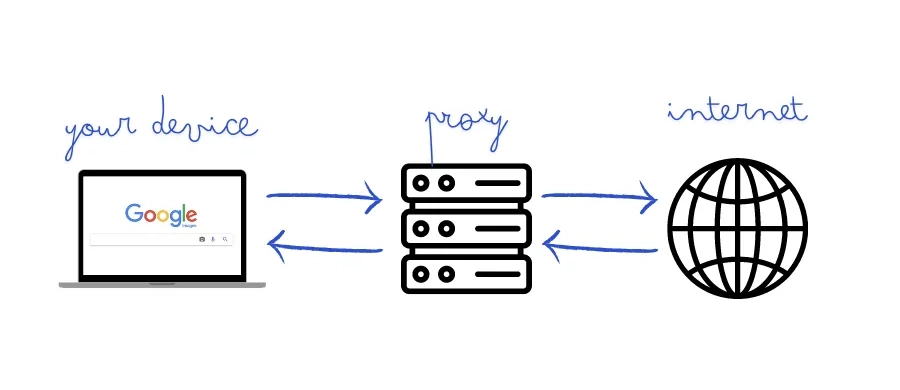
Diagram: A proxy server acts as a go-between for your device and the internet.
Essentially, the website you visit only sees the proxy server's IP address, effectively masking or changing your original IP address.
Why You Need a Proxy in Today's Online World
Changing your IP address might sound simple, but it opens up a world of possibilities for controlling your online presence:
- Enhanced Online Anonymity and Privacy: By hiding your real IP, it becomes much harder for websites and advertisers to track your activity across different sites and build a profile about you based on your network location.
- Accessing Geo-Restricted Content: Some websites, streaming services, or online content are only available to people in specific countries or regions. Using a proxy with an IP address in the required location allows you to bypass these geographical restrictions.
- Basic Security Layer: Proxies can add a basic layer of security by filtering some malicious traffic or acting as a buffer between your device and the open internet.
- Managing Multiple Online Accounts (The Bridge to Your Product): Explain that many online platforms (social media, e-commerce, advertising networks) try to detect if one person is controlling multiple accounts, often by looking at the IP address. Using a single IP for multiple accounts is a major red flag. This is the crucial link.
Understanding Different Types of Proxies
Not all proxies are created equal. They differ based on their origin, how they are used, and their level of anonymity. Here are the main types you'll encounter:
| Type | Source of IP Address | Pros | Cons | Best For |
|---|---|---|---|---|
| Datacenter Proxies | Servers located in data centers | Very fast, Generally cheaper | Can be easily detected as proxies, Not associated with real users | Scraping non-sensitive public data, High-volume simple tasks |
| Residential Proxies | Real IP addresses from home/mobile internet users | Very hard to detect as proxies, Appear as regular users, High trust | Slower than datacenter, More expensive than datacenter | Managing sensitive accounts (social media, e-commerce), Accessing strict sites, Geo-targeting |
| Mobile Proxies | IP addresses from mobile network carriers (3G/4G/5G) | Highest level of trust, IPs are often dynamic (change frequently) | Most expensive, Speed depends on mobile network quality | Managing highly sensitive accounts, Mobile-specific tasks, Activities requiring the highest anonymity |
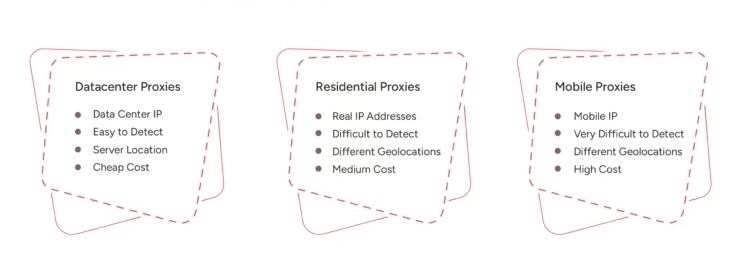
Different types of proxies offer varying levels of speed, cost, and anonymity.
Static vs. Rotating Proxies
- Static: You get one fixed IP address that doesn't change. Good for maintaining a consistent "location" for a specific task or account.
- Rotating: You get access to a pool of IPs, and the proxy automatically assigns you a new IP address at regular intervals or with each new connection request. Excellent for scraping or tasks where you need to distribute requests across many IPs quickly to avoid being blocked.
HTTP/HTTPS vs. SOCKS
- HTTP/HTTPS: Designed for web traffic. HTTPS proxies can handle encrypted connections.
- SOCKS (SOCKS4/SOCKS5): More versatile. Can handle various types of internet traffic, not just web browsing. SOCKS5 is the most common and supports authentication and IPv6. For general use and flexibility, SOCKS5 is often preferred.
Proxy vs. VPN: What's the Difference?
Beginners often confuse proxies and VPNs (Virtual Private Networks). While both route your traffic through another server and change your visible IP, they operate at different levels:
- Proxy: Typically works at the application level (e.g., just your web browser or a specific app). It changes your IP for that specific application's traffic. It doesn't usually encrypt your connection by default (though HTTPS proxies handle already-encrypted traffic).
- VPN: Works at the operating system level, creating a secure, encrypted tunnel for all your internet traffic from your device. It changes your IP address for everything connected through the VPN and adds a strong layer of security/encryption to your entire connection.
Proxy changes IP for specific apps; VPN changes IP and encrypts all traffic.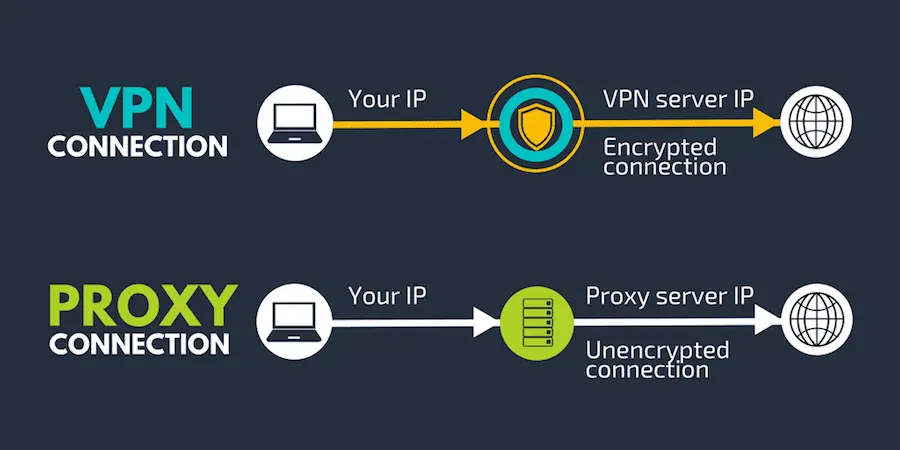
For tasks requiring managing multiple independent online identities (like multi-accounting), proxies are often preferred because you can assign a different proxy to each separate account/browser profile, something that's harder or impossible to do with a single VPN connection covering your whole device.
The Limitation: Why Just a Proxy Isn't Always Enough
You've got your proxy, your IP address is hidden... you're good to go, right? Not entirely.
While changing your IP is essential, modern websites and advanced tracking systems look at much more than just your IP address to identify you. They also collect data about your browser and device settings, creating what's known as a "browser fingerprint."
Your browser fingerprint includes details like:
- Your User Agent (browser type, version, OS)
- Installed fonts
- Screen resolution
- Canvas fingerprinting (how your browser renders graphics)
- WebGL fingerprinting
- Hardware details (like graphics card)
- Browser plugin list (though less common now)
- Language settings
- Do Not Track status
If you try to manage multiple accounts using just a standard browser, even if you switch proxies for each account, your underlying browser fingerprint remains the same. To a sophisticated website, it will look like multiple different "people" are all using the exact same type of computer and browser in the exact same way, just connecting from different locations (IPs). This is a massive red flag and can still lead to detection, linking of accounts, or blocks.
Websites collect many data points beyond your IP to create a unique browser
fingerprint.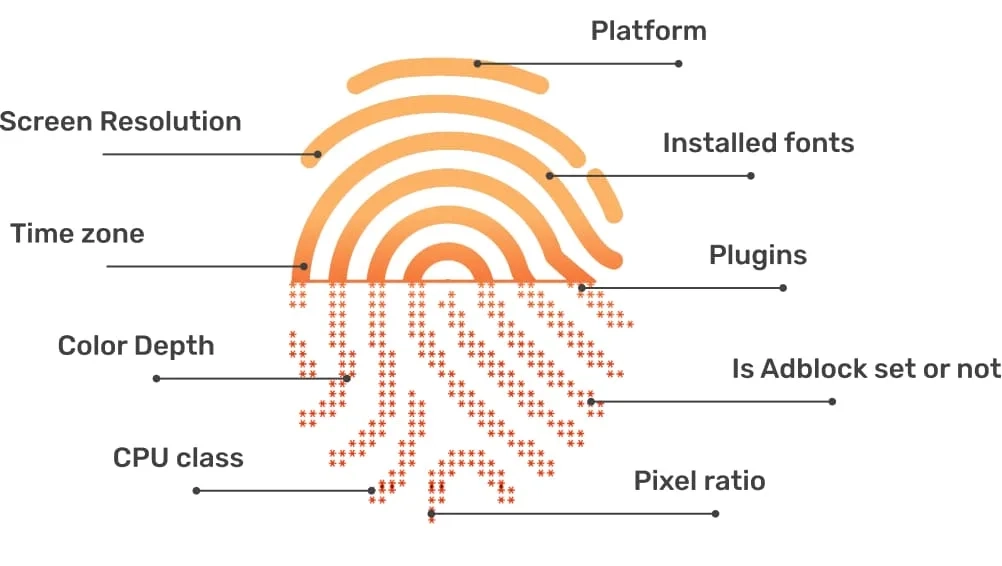
Taking Anonymity to the Next Level: Introducing Antidetect Browsers
This is where Antidetect Browsers come into play, and why they are the essential partner for proxies when you need serious online control and anonymity, especially for multi-accounting.
An antidetect browser is a specialized tool designed to create and manage multiple, completely independent browser profiles. Each profile within an antidetect browser is designed to have a unique, consistent, and natural-looking browser fingerprint.
Think of it like this: While a proxy gives each of your online identities a different mailing address (IP), an antidetect browser gives each identity a unique set of physical characteristics (the browser fingerprint) – different clothes, different handwriting, slightly different mannerisms.
The Synergy: Proxies + Antidetect Browser = True Independence
Here's the key point: For powerful, reliable online identity management, you need both:
- A unique IP address for each profile (provided by the proxy).
- A unique, consistent browser fingerprint for each profile (provided by the antidetect browser).
Combining proxies and an antidetect browser creates truly independent online
identities.
An antidetect browser like WhoLogin makes managing this combination incredibly simple. Instead of manually configuring network settings every time you switch accounts or using clunky third-party tools, you can:
- Create a new browser profile for each online identity.
- Assign a specific proxy (Datacenter, Residential, Mobile) directly to that profile within the browser's settings.
- The browser automatically handles giving that profile a unique, convincing fingerprint.
- When you open that profile, it automatically uses the assigned proxy and its unique fingerprint, creating a fully isolated and distinct online session.
This seamless integration is why antidetect browsers are indispensable tools for anyone serious about online privacy, security, data scraping, or managing multiple accounts effectively and safely.
Conclusion: Proxies Are Just the Beginning
Understanding proxies is a fundamental step towards taking control of your online presence. They are powerful tools for masking your IP, accessing restricted content, and forming the network layer for managing multiple online identities.
However, as online tracking becomes more sophisticated, relying on proxies alone is often insufficient. Combining the IP-masking power of proxies with the unique browser fingerprint management of an antidetect browser like WhoLogin provides the comprehensive solution needed for true online anonymity, security, and successful multi-account management.
Ready to experience the power of truly independent online profiles?
Explore how WhoLogin simplifies proxy management and unlocks advanced online capabilities!